It’s hard to begin talking about technology strategy unless you have a full grasp on the technology in use today, how well it is being used, and whether it is fully meeting the needs for which it was bought. For organizations that distribute responsibility for purchasing technology across the company, either functionally or geographically, cataloging all the technology in use may entail a significant effort.
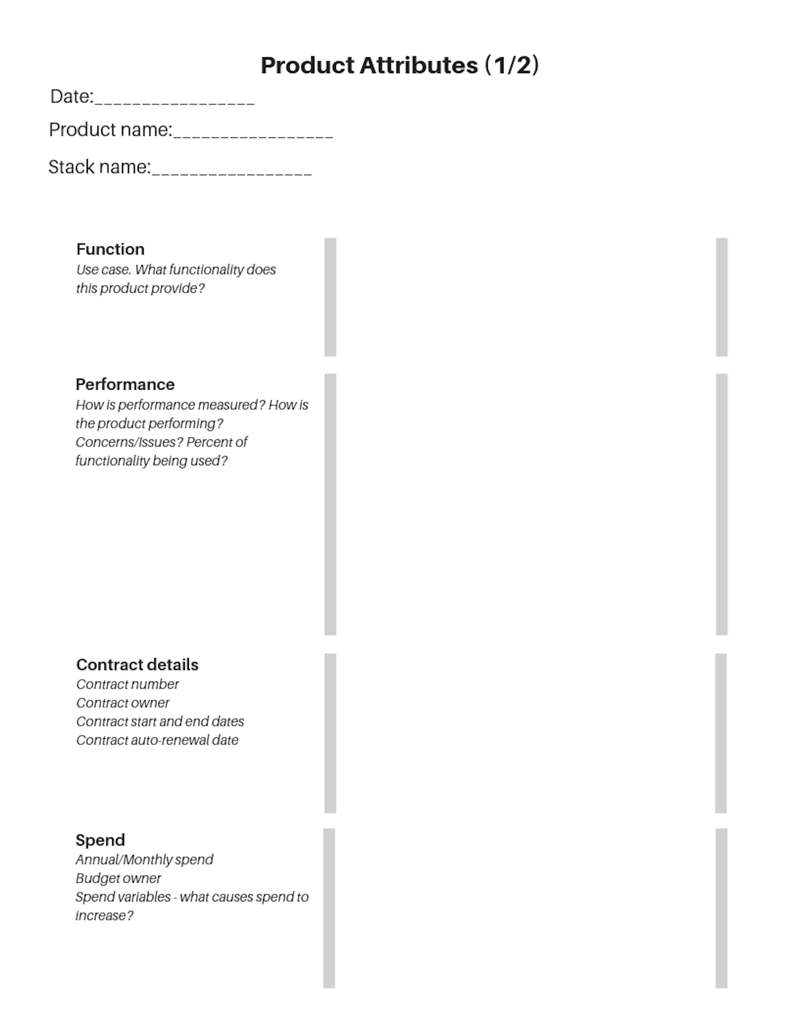
Product Attributes
As you think about cataloging all of your technology, it’s important to define what information you need to collect about each product. We’ve seen companies track as many as 50 different attributes for each product they use.
Not sure what details to collect? We recommend starting with the following:
Function
- Use case—What functionality does this product provide?
Performance
- Performance measurement—How is performance measured?
- Performance assessment—How well is this product performing? I recommend developing a scale or assessment process to create some uniformity in rating products across the stack.
- Any concerns or issues with the product and how it performs
- Percent of functionality being used
Contract Details
- Contract number
- Contract owner (who at your company “owns” this product)
- Contract start date
- Contract end date
- Auto-renewal date
Spend
- Annual and monthly spend
- Spend variables (what causes spend to increase?)
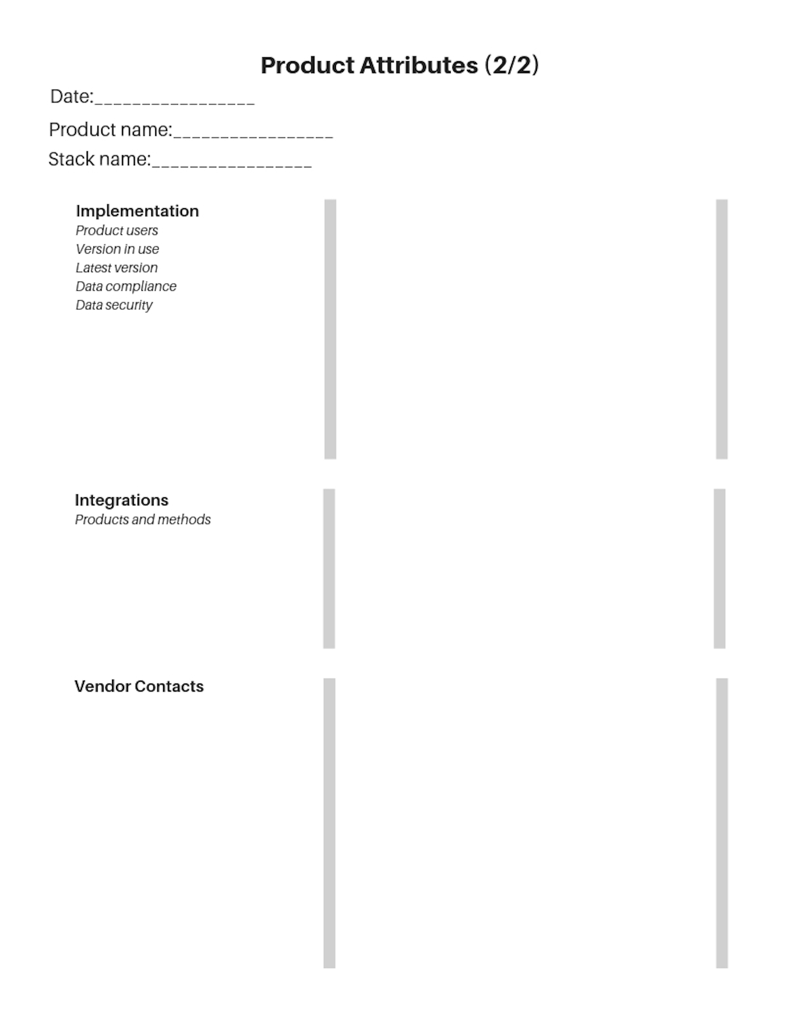
Implementation
- Product owner
- Product users
- Version in use
- Latest version
- Integrations and method of integration (possibly the most critical piece of information to collect, because disconnecting a product in your stack that has been integrated with several others can bring your entire stack tumbling down if not handled carefully). You should be tracking integration at the field level and noting whether the integration is one way or bi-directional.
- Does this product meet data compliance requirements?
- Has this product been assessed for data security risks? This won’t be applicable for all products. If you have a well-controlled procurement process, you may not need to look at this.
Vendor Information